❏ What is Lychee SAML Authentication?
Lychee SAML Authentication is a plugin which allows Redmine and an IdP (Identity Provider) to communicate with SAML authentication information, thereby enabling single-sign-on.
Compatible IdPs are OneLogin and ADSF (Active Directory Federation Services).
❏ OneLogin
1. IdP (Identity Provider) Settings
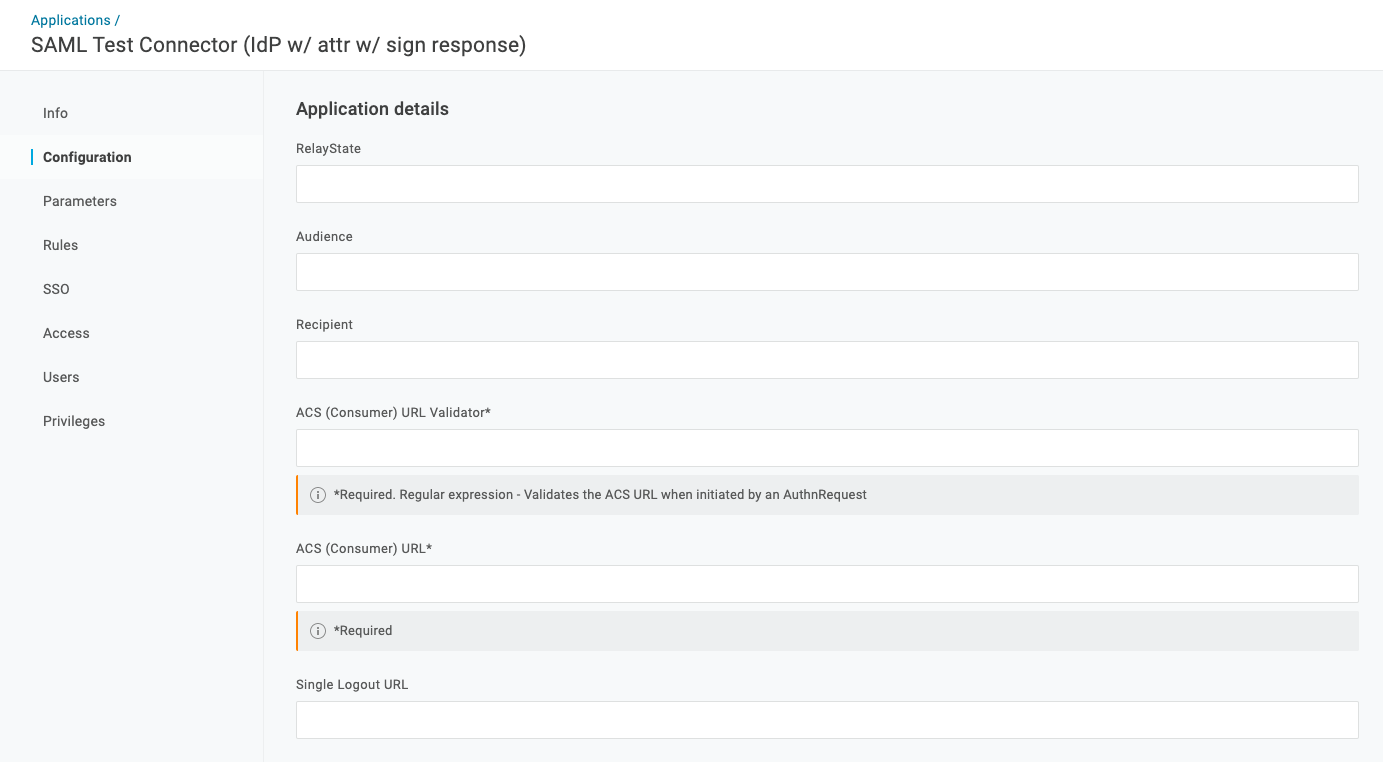
- Display the Configuration screen of the application registered for use with Redmine
In the Administration > Applications menu, go to [Applications] > Application registered for Redmine > Configuration. - Input the following and click [Save]FieldValueAudiencePart of the URL ending in “metadata” found under [Issuer URL] on the SSO screen
For the URL “https://app. onelogin.com/saml/metadata/abcdefg-hijklmn”, enter:
https://app. onelogin.com/saml/metadataRecipientURL displayed under “Recipient” on the SAML Authentication screen.
It has the following format:
Redmine’s URL/auth/one_login/callbackACS (Consumer) URL ValidatorRegular expression for “ACS URL Validator” displayed on SAML Authentication screen.ACS (Consumer) URL”ACS URL” displayed on SAML Authentication screen.
2. Plugin Settings
- Display the SAML Authentication screen
Administration > SAML authentication - Click the [SAML Authentication] link
The SAML Authentication screen will be displayed - Click [+SAML Authentication] in the top right of the screen
New authentication form - Enter the following and click the [Create] buttonFieldValueTypeOne LoginNameAny nameDomainRedmine’s URLApp IDPart of the URL path after “metadata/” found under [Issuer URL] on the SSO
screen(*1). For the URL “https://app. onelogin.com/saml/metadata/abcdefg-hijklmn”,
enter: “abcdefg-hijklmn”SSP slo IDPart of the URL path after “slo/” found under [SLO Endpoint(HTTP)] on the SSO
screen(*1). For the URL “https://example.onelogin.com/trust/saml2/http-redirect/
slo/1234567890″, enter: “1234567890”IDP Cert AlgorithmThe same algorithm found under [SAML Signature Algorithm] on the SSO screen(*1)IDP Cert FingerprintThe value found under [Fingerprint] on the Certificates screen(*2)1 In the Administration > Applications menu, go to [Applications] > Application registered for Redmine > SSO 2 In the Administration > Applications menu, go to [Applications] > Application registered for Redmine > SSO > [X.509 Certificate], and click the [View Details] link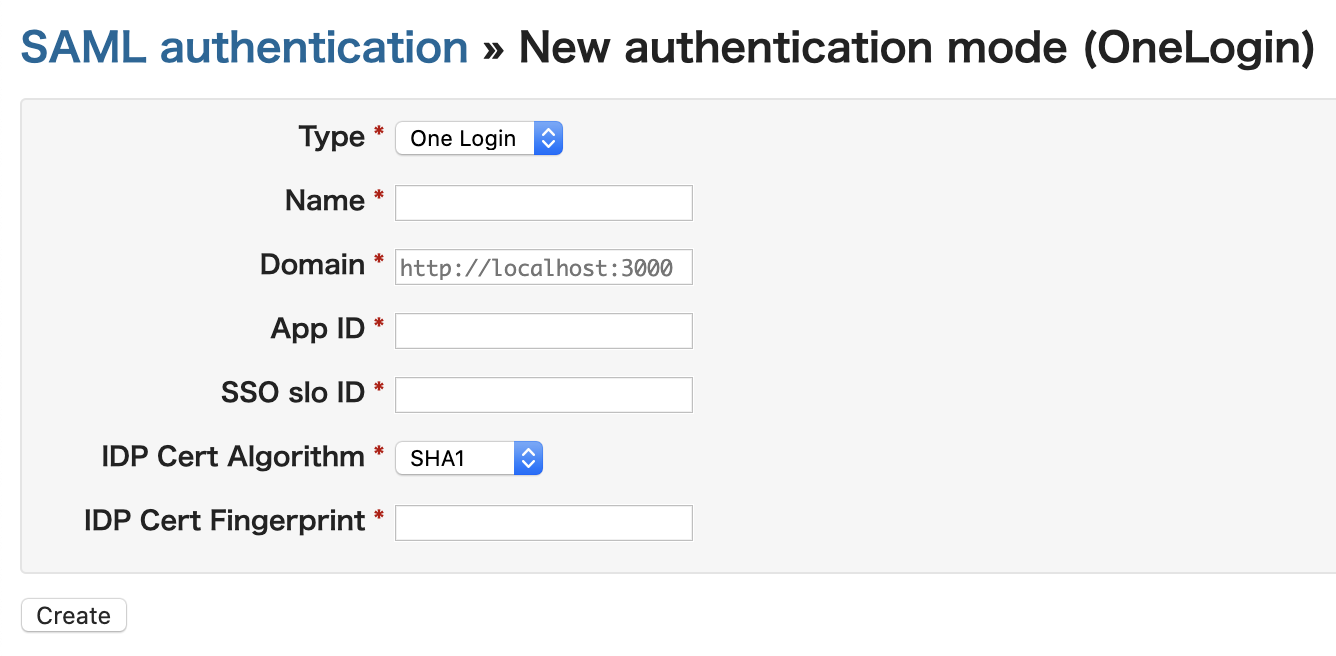
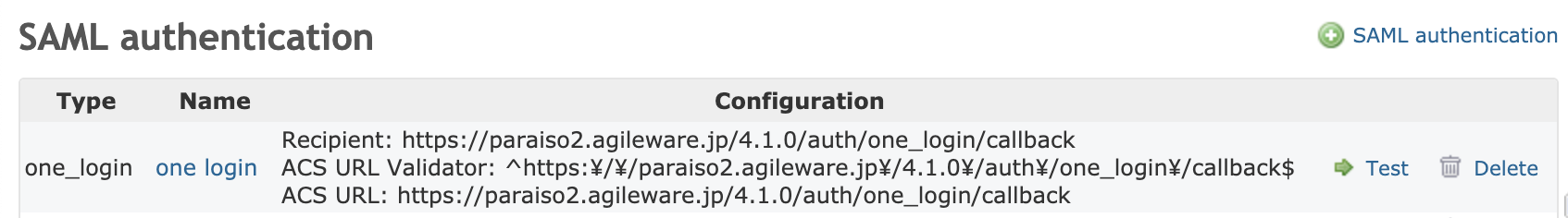
- Setup information will appear in OneLogin’s Configuration
The following information will appear on the SAML Authentication screen:- Recipient
- ACS URL Validator
- ACS URL
❏ ADFS(Active Directory Federation Services)
1. IdP (Identity Provider) Settings
- Display the application registered for use with Redmine Home > Azure Active Directory > Application Registration > Application registered for Redmine
- Display [Brand], enter the following in [Homepage URL], and click [Save]
Enter the URL using the following format:Redmine's URL/auth/adfs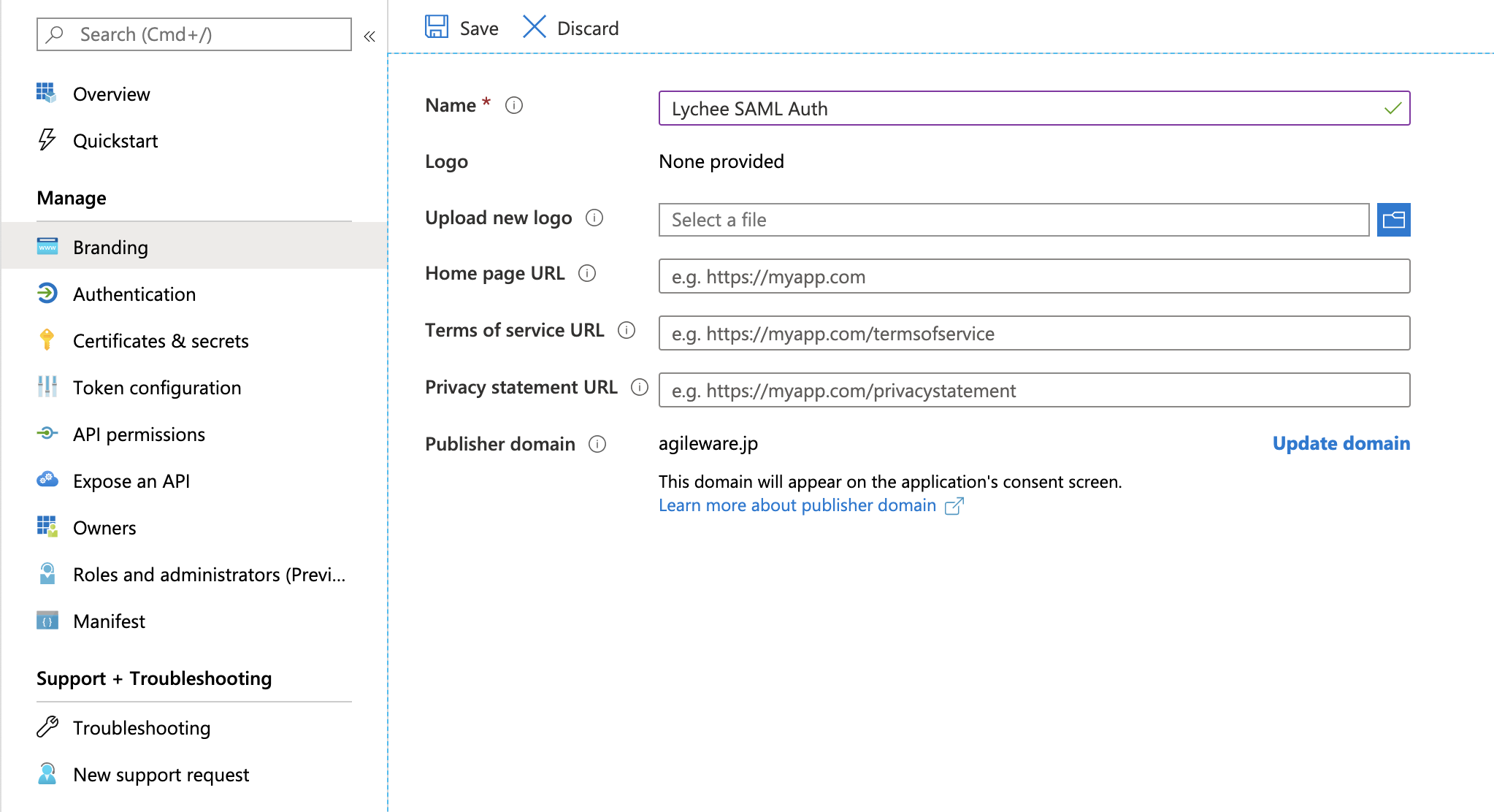
- Display [Authentication], enter the following in [Web > Redirect URI], and click [Save]FieldValueWeb > Redirect URIURI with the following format:
Redmine’s URL/auth/adfs/callbackWeb > Logout URLURL with the following format:
Redmine’s URL/logout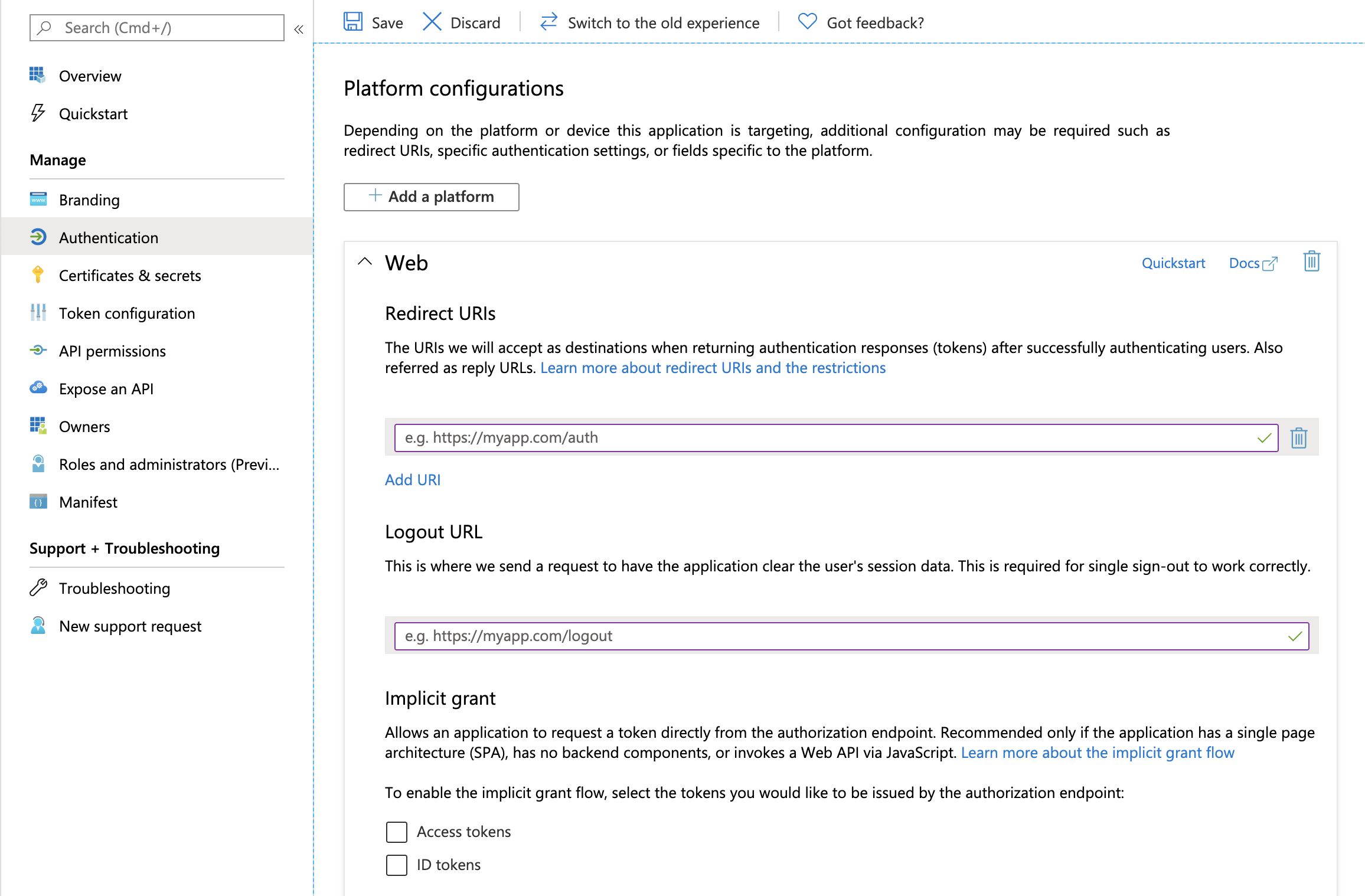
- Display [Certificates and Secrets] and upload the certificate
2. Plugin Settings
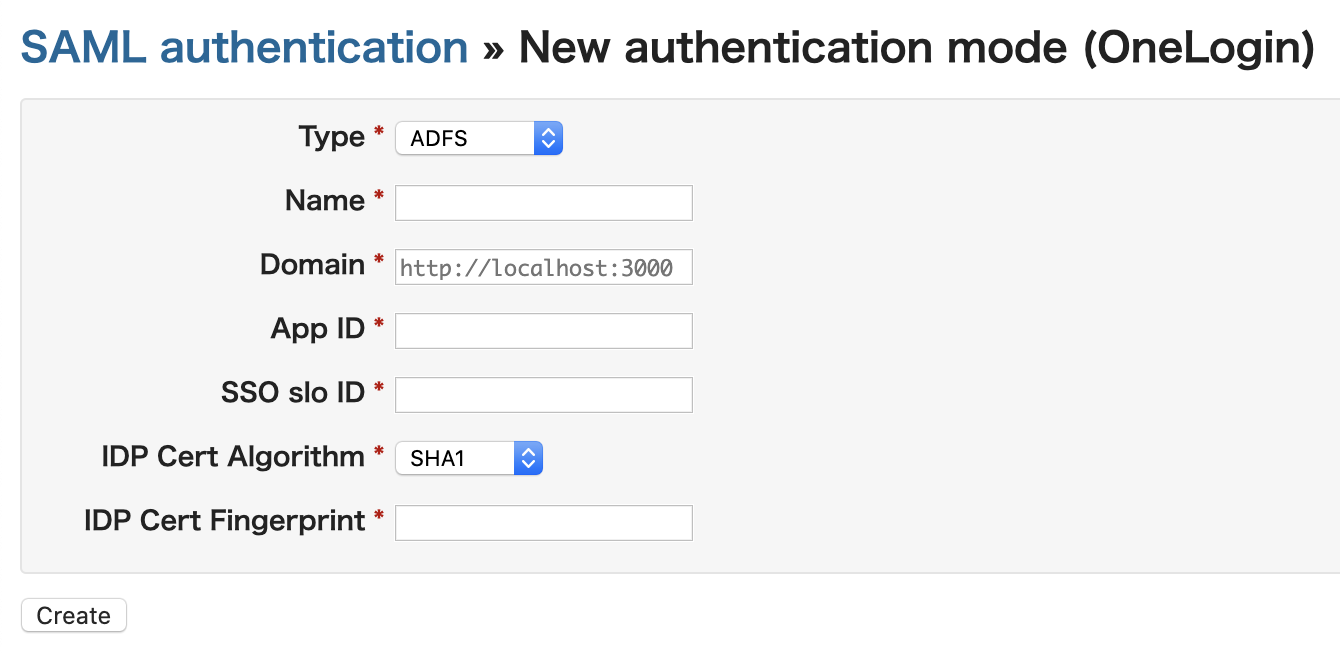
- Display the SAML Authentication screen
Administration > SAML authentication - Click the [SAML Authentication] link
The SAML Authentication screen will be displayed - Click [+SAML Authentication] in the top right of the screen
New authentication form - Enter the following and click the [Create] buttonFieldValueTypeADFSNameAny nameDomainRedmine’s URLApp ID[Application (Client) ID] on the Overview screen(*1) of the application registered for RedmineSSP slo ID[Directory (Tenant) ID] on the Overview screen(*1) of the application registered for RedmineIDP Cert AlgorithmAlgorithm used when creating the FingerprintIDP Cert FingerprintFingerprint for token-signing certificate*1 Azure Home > Application Registration > Application for Redmine > Overview
3. Requesting a Fingerprint for a Token-signing Certificate
- Check the Federation Metadata endpoint
Application Registration > Endpoint > Federation Metadata Endpoint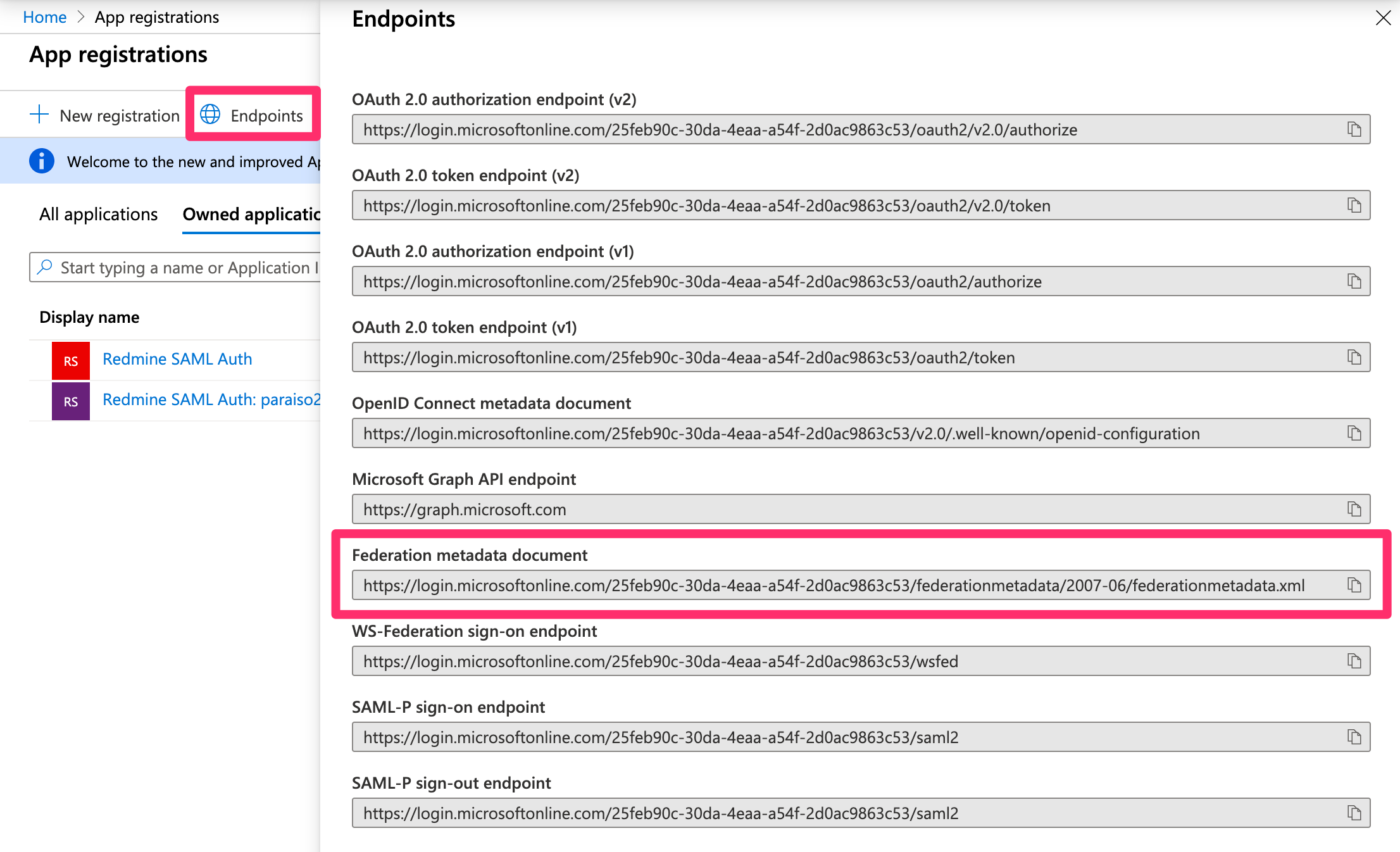
- Access the endpoint
Metadata XML will be displayed. - Copy the entire metadata and paste it in a text editor
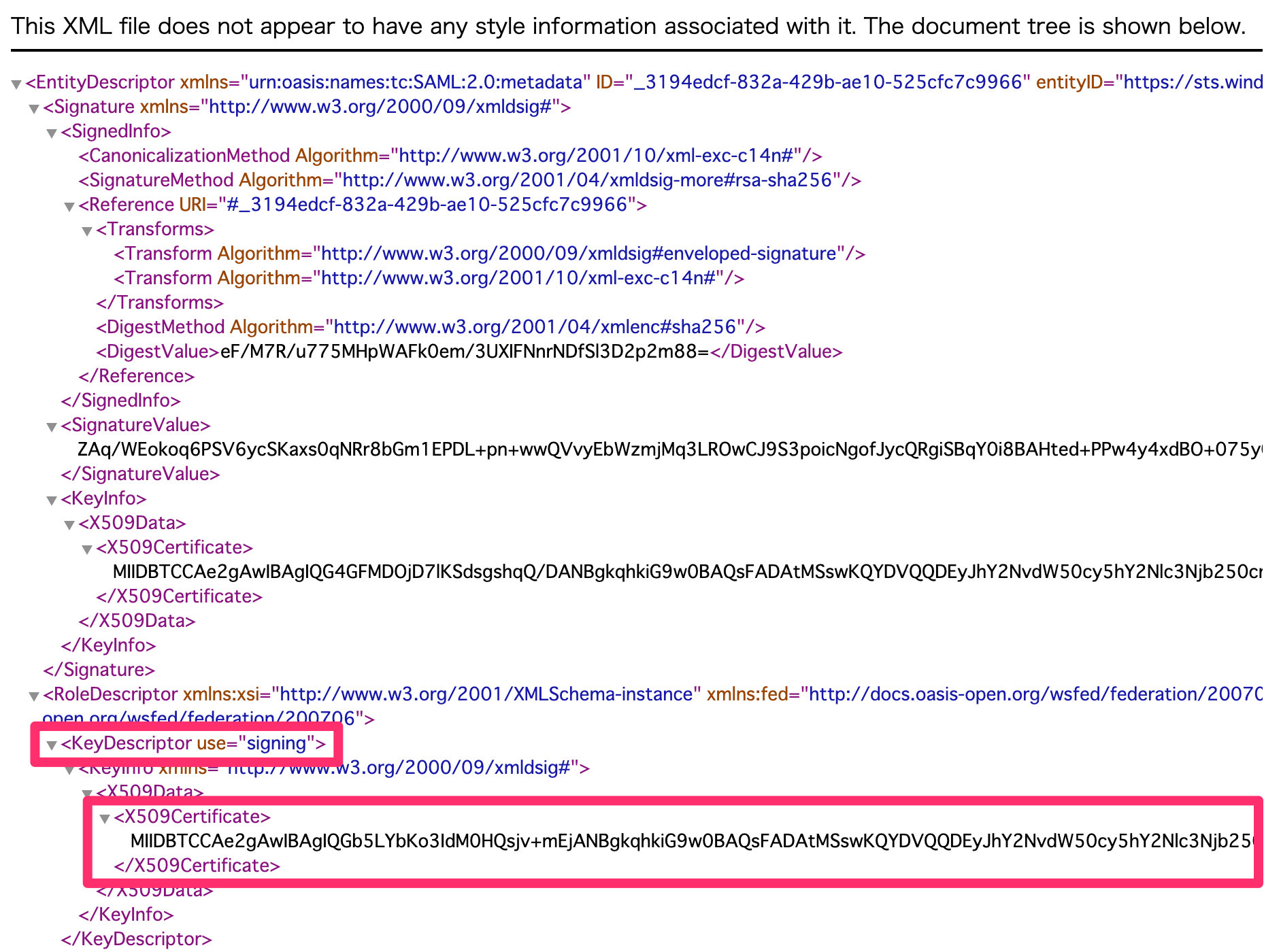
Copying only theX509Certificatevalue can sometimes fails, so copy the entire screen and paste it in a text editor. - Create a CRT file
Create a CRT file using theX509Certificatevalue subordinate to theKeyDescriptorelement which hassigningas itsuseproperty.
The CRT file’s structure is as follows:- Line 1: —–BEGIN CERTIFICATE—–
- Line 2:
X509Certificate‘s value - Line 3: —–END CERTIFICATE—–
- Request a Fingerprint from the CRT file created in (4)
If you are usingOpenSSL, request it using the following command:openssl x509 -[hash algorithm] -fingerprint -in [path of CRT file generated in (4)] -nooutExample: If the hash algorithm is “sha512” and the path of the CRT file created in (4) is “path/to/x509.crt”openssl x509 -sha512 -fingerprint -in path/to/x509.crt -noout
コメント